08. Understanding Testing Methods and Tools
Understanding Testing Methods and Tools
ND545 C3 L2 A06 Understanding Testing Methods And Tools
Overview
To understand if an organization may be vulnerable to attacks businesses can do different levels and types of testing to identify vulnerabilities and proactively address them. This process of identifying gaps is a foundational part of the overall vulnerability management process.
Finding Gaps Through the Vulnerability Management Process
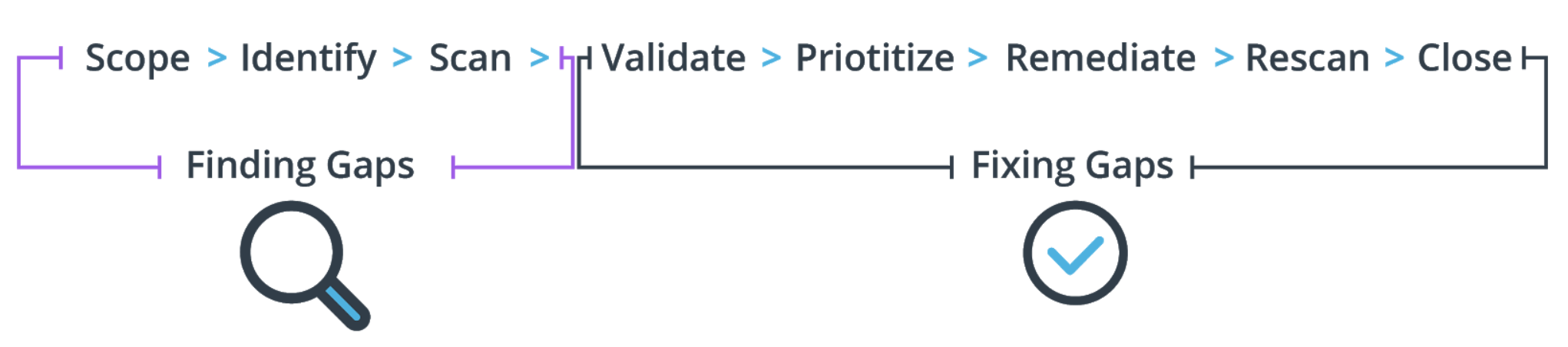
Scope: Determine, conceptually what you want to test. For example, you can target a certain data center looking for a specific set of issues, a specific application, or other reasons.
Identify: Pinpoint the specific host, network, application, or other resource targets. Here you may identify specific IP addresses or URLs for example.
Scan: Configure and run the scan or test against the identified target. Here you are using various tools and methods, such as vulnerability scanning software, to find the issues.
Common Testing Methods for Finding Vulnerabilities
Host and network vulnerability scans are used to find vulnerabilities on servers, desktop, mobile devices, etc. within a network. Active vulnerability scanning used to traffic and actions to identify vulnerabilities. Passive scanning listens on the system and identifies issues in server and client software.
Application vulnerability scans target security within code and its operation. The dynamic application scans test functionality while the program is executing operations, while static scans test functionality without running any code.
Penetration testing is another level of actively trying to see if you can essentially break security. Penetration tests can target networks, hosts, people, and physical assets.
Reference: NIST CRSC Glossary